Role-Based Access Control (RBAC)
The Role-Based Access Control (RBAC) module lets you define what actions users can perform. You create roles (or use defaults), assign them to users, and the system enforces permissions at runtime. When a user attempts an action outside their permissions, a warning is triggered.
Plans and Capabilities
Starter Plan
- Use default roles: Admin and Operator.
- No custom role creation.
Business Plan
- Create customized roles with granular permissions.
- Invite users and assign any default or custom role.
Accessing RBAC and Inviting Users
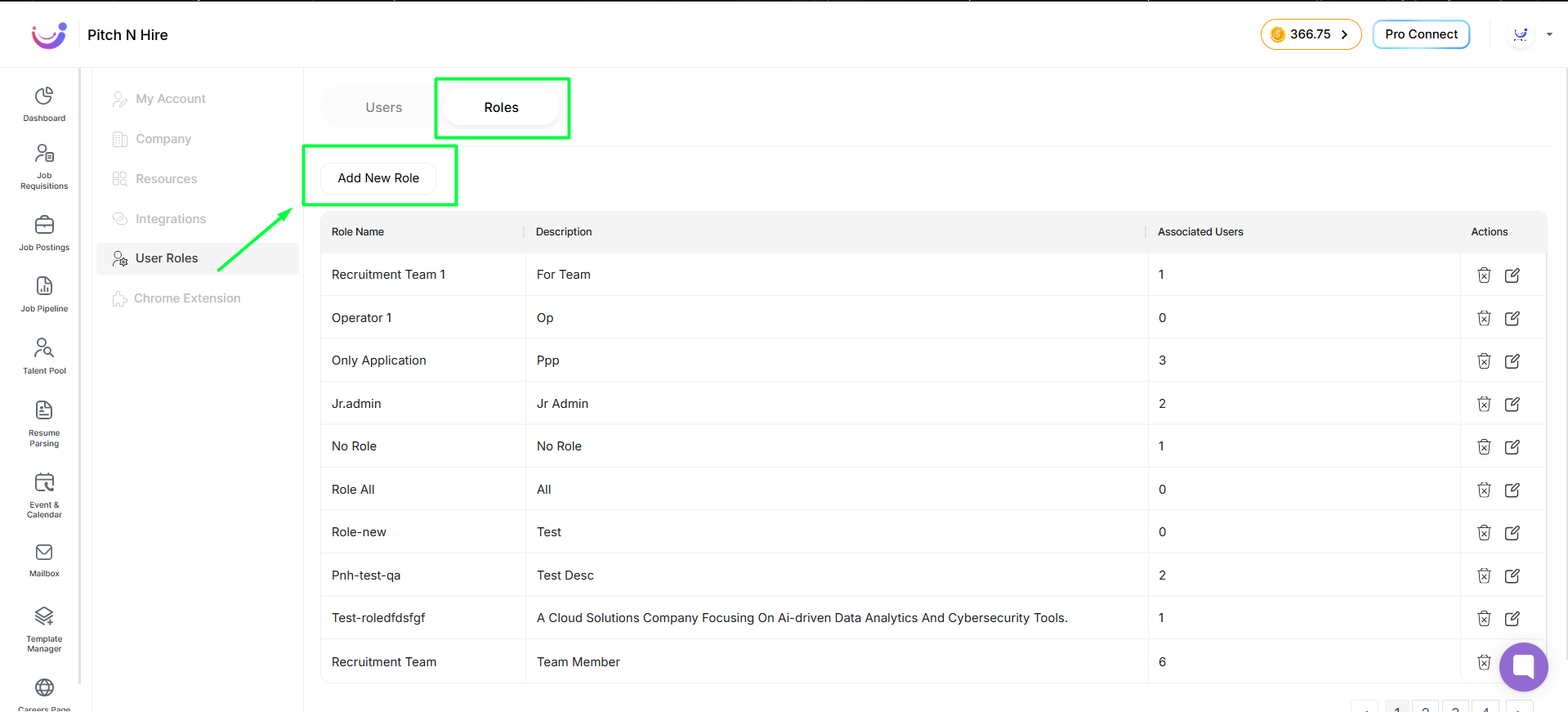
- Go to Settings → User Roles to manage roles.
- Click Roles (Business plan) to define permissions & then on Click on Add New Role.
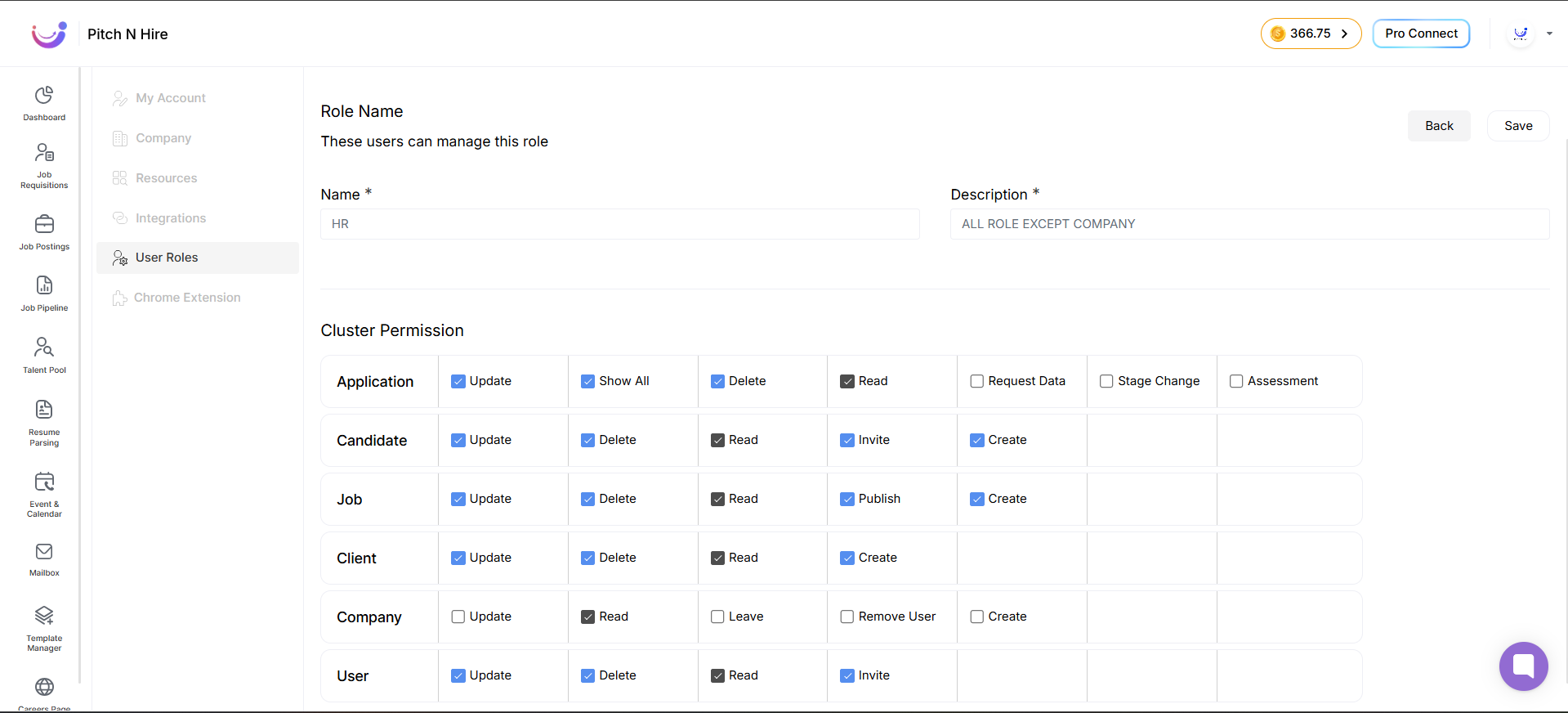
- Fill the Details Role Name & Description, Choose the Permissions.
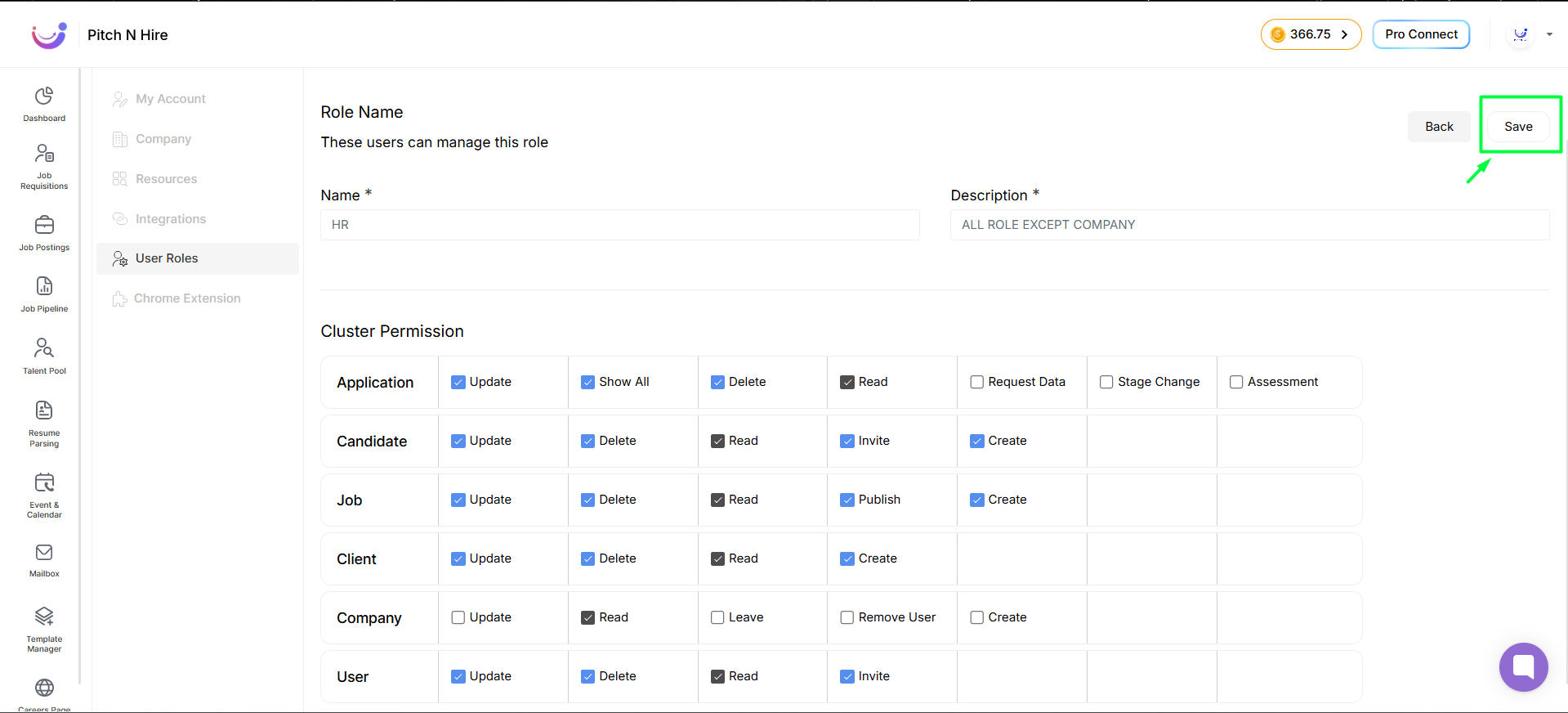
- then Click on Save
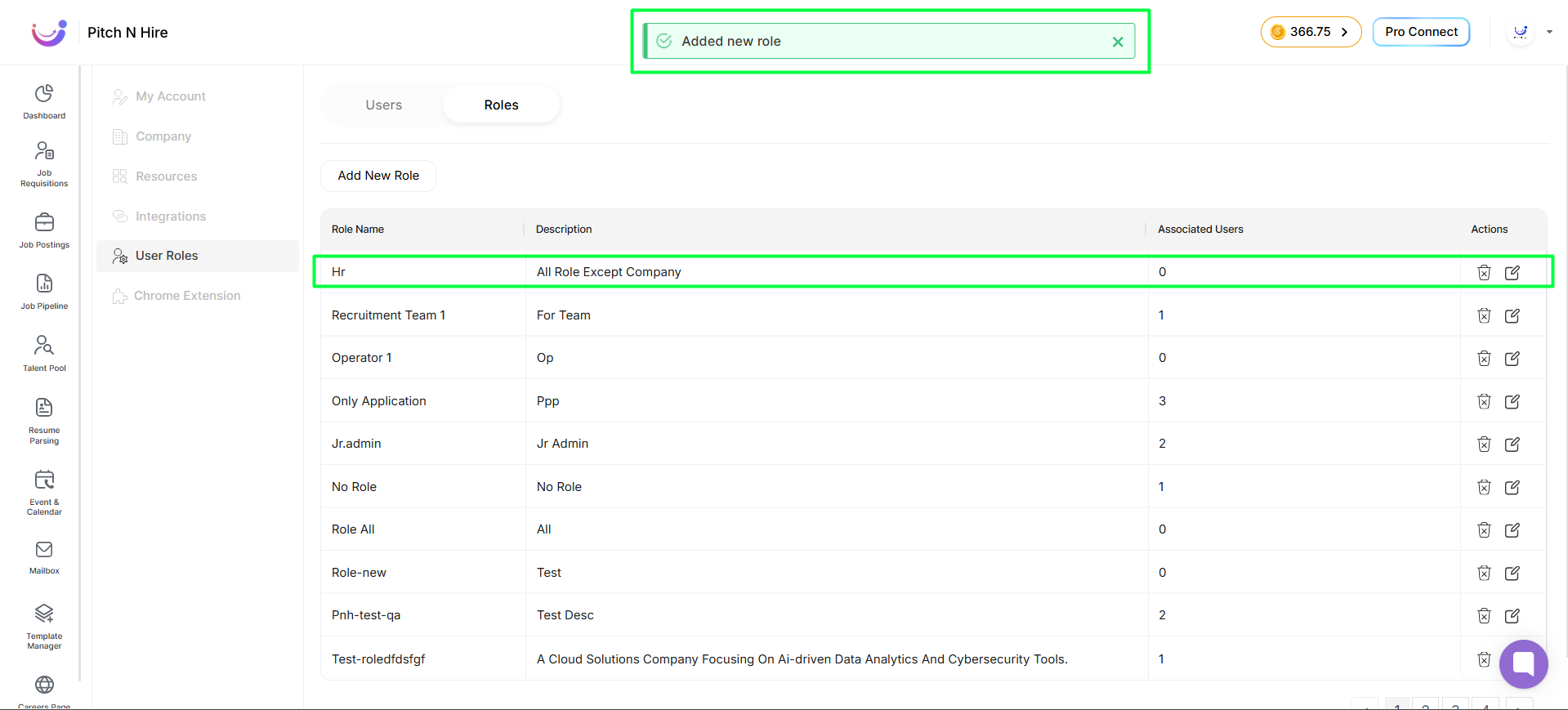
- Role Created Successfully
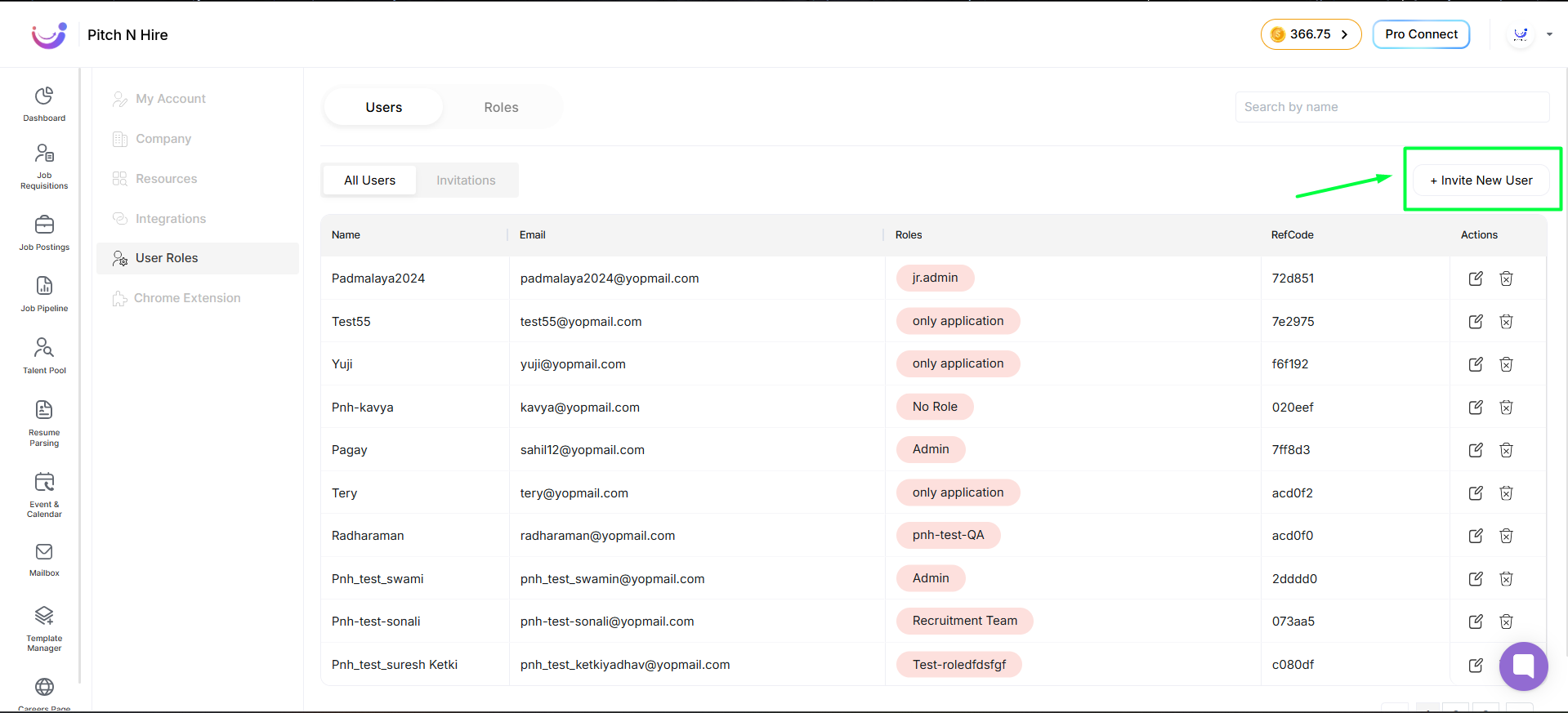
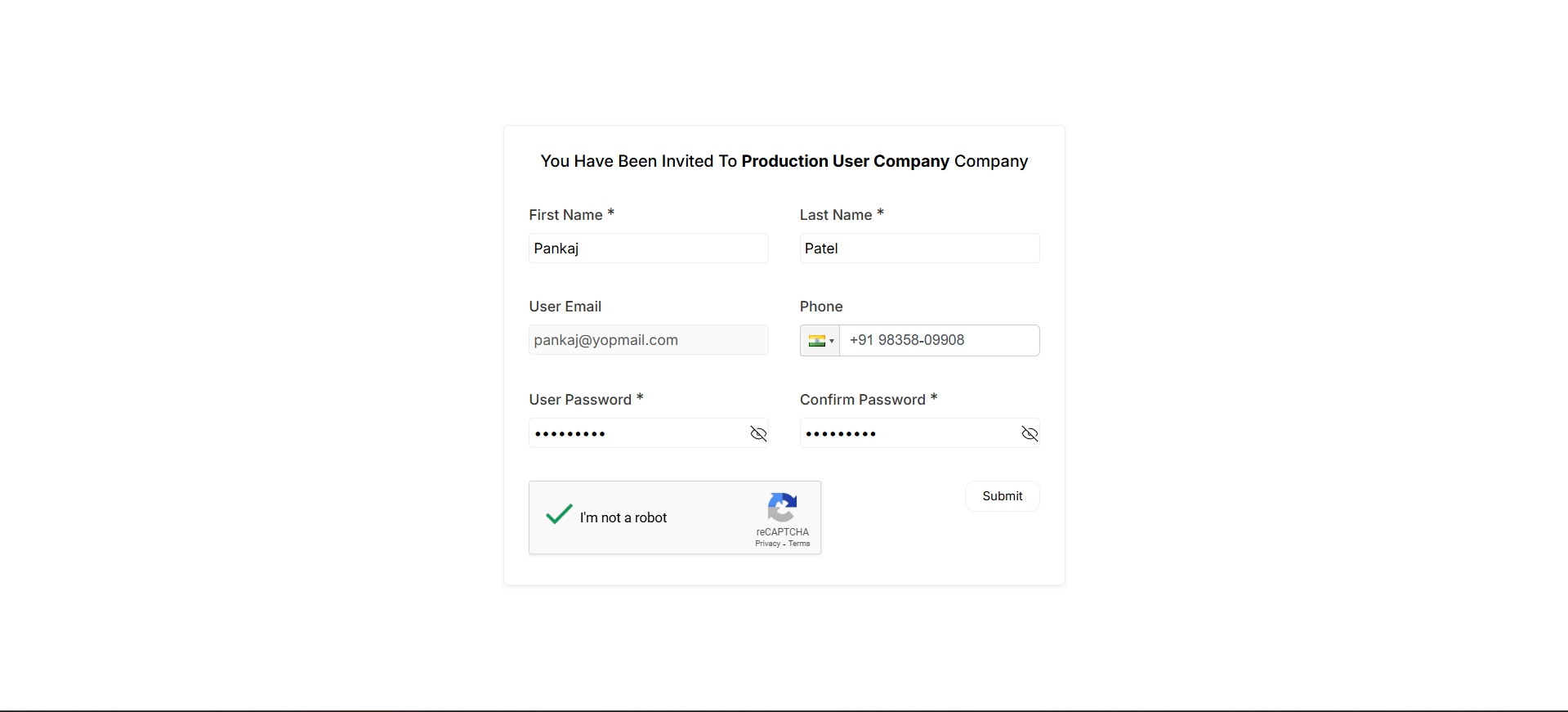
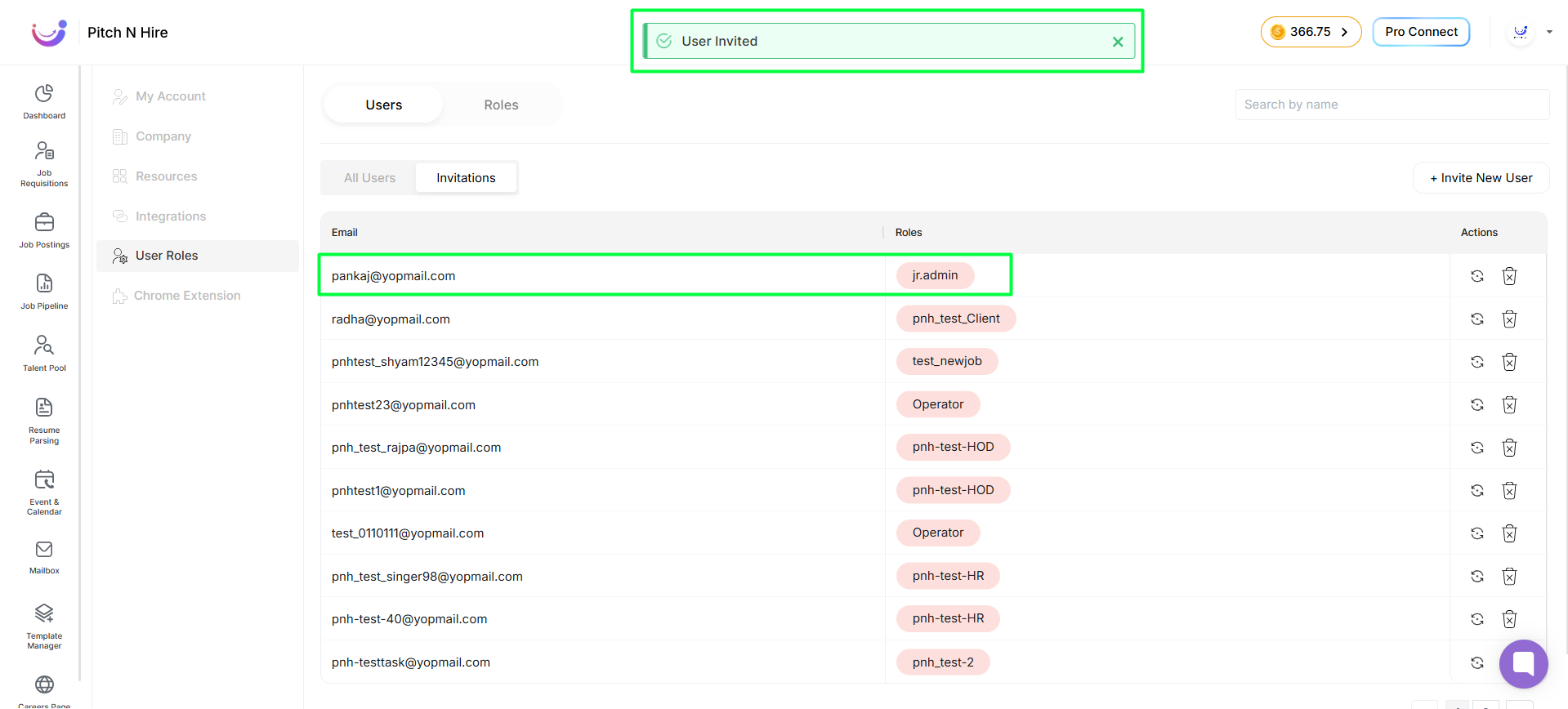
- Go to Settings → Users to invite users.
- Click Invite User
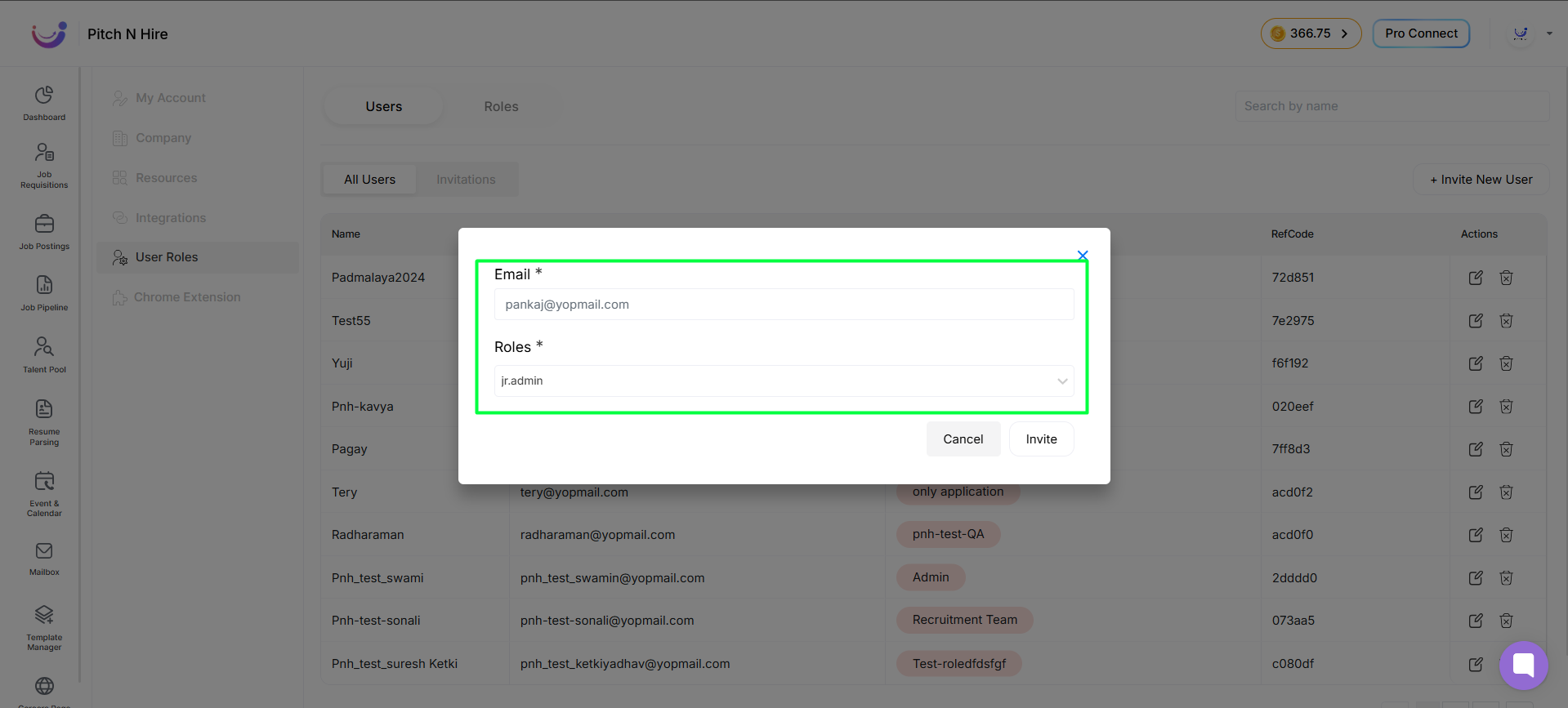
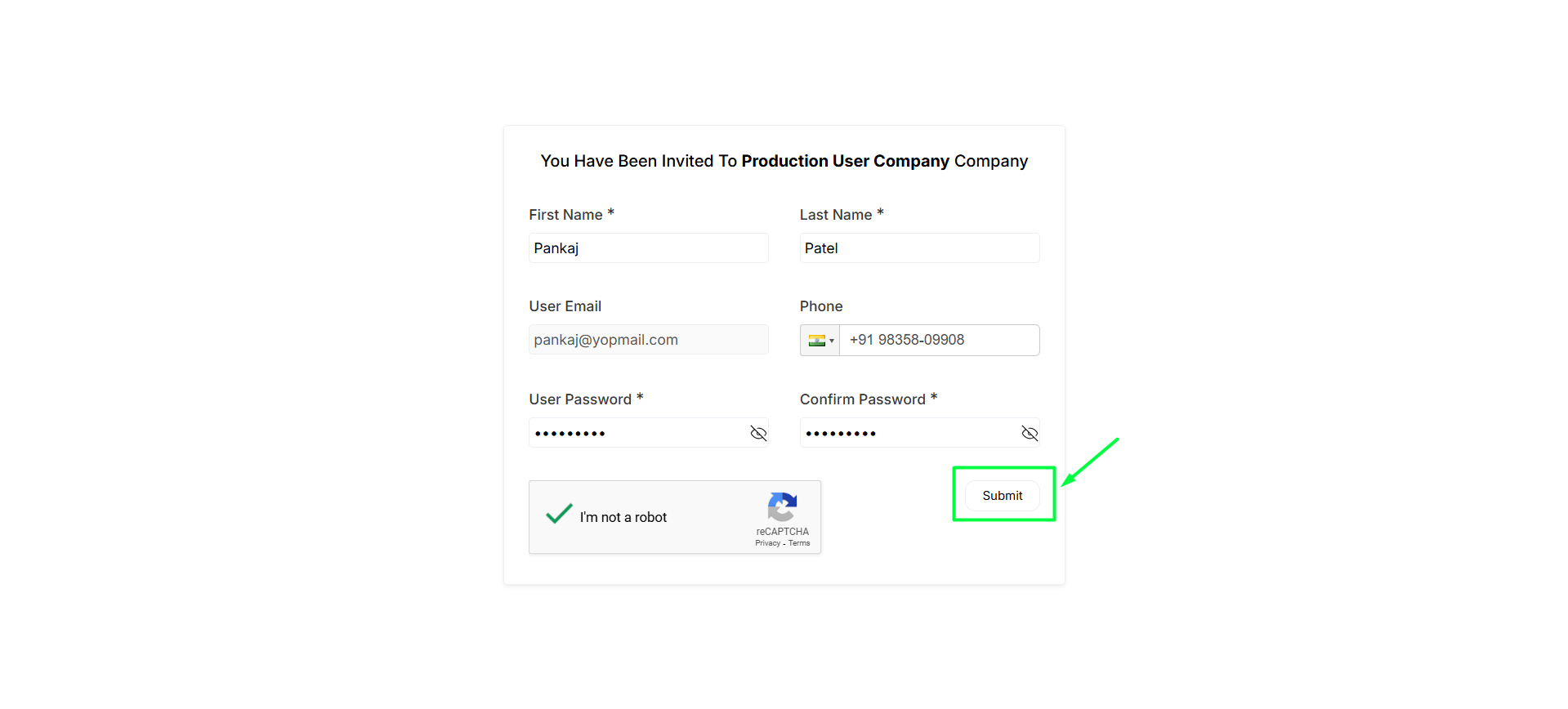
- Enter Email and select a Role
- then Click on Invite.
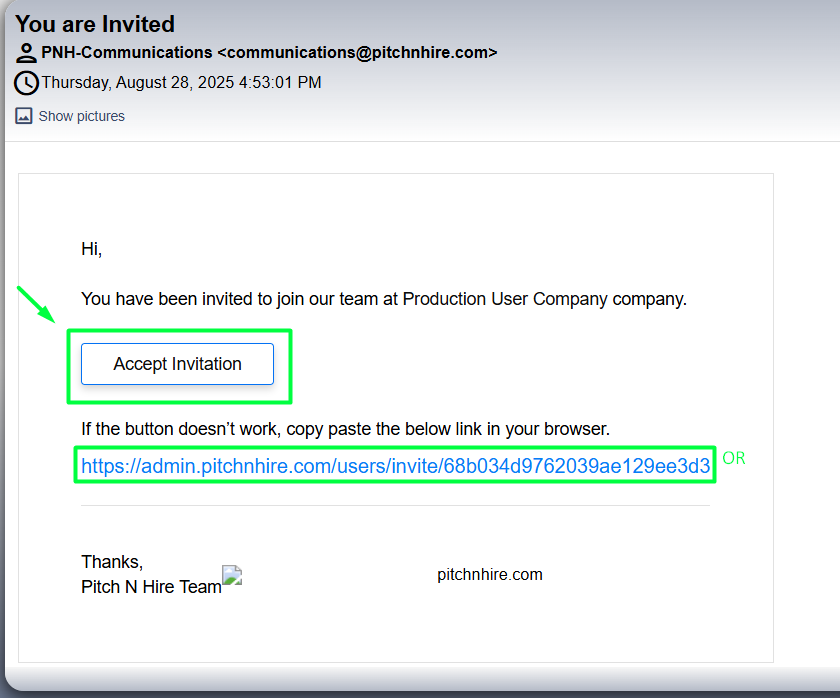
- An invitation email is triggered to the user. click on Accept Invitation or Copy the URL
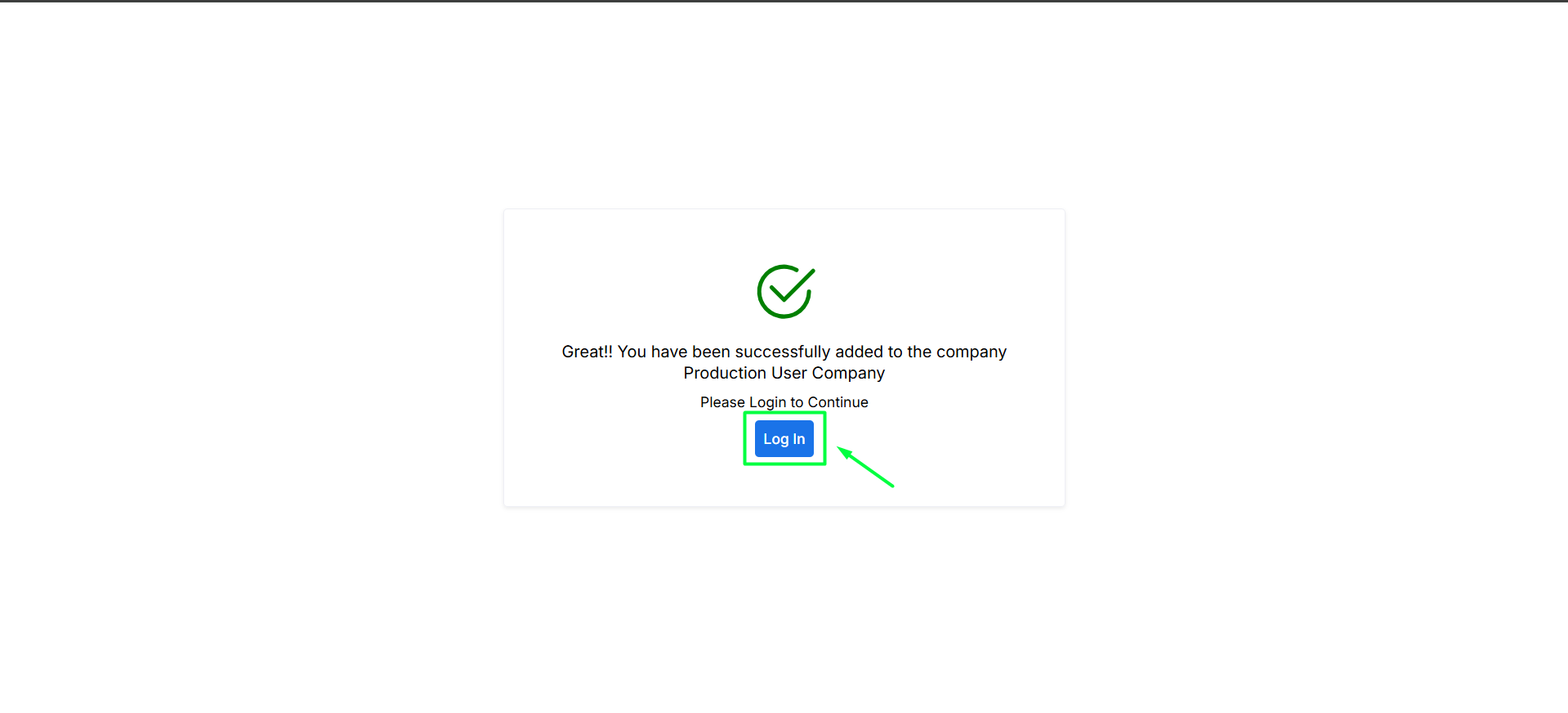
- The invited user completes signup and signin as a team member.
- Signup Fill Details
- Click on Submit
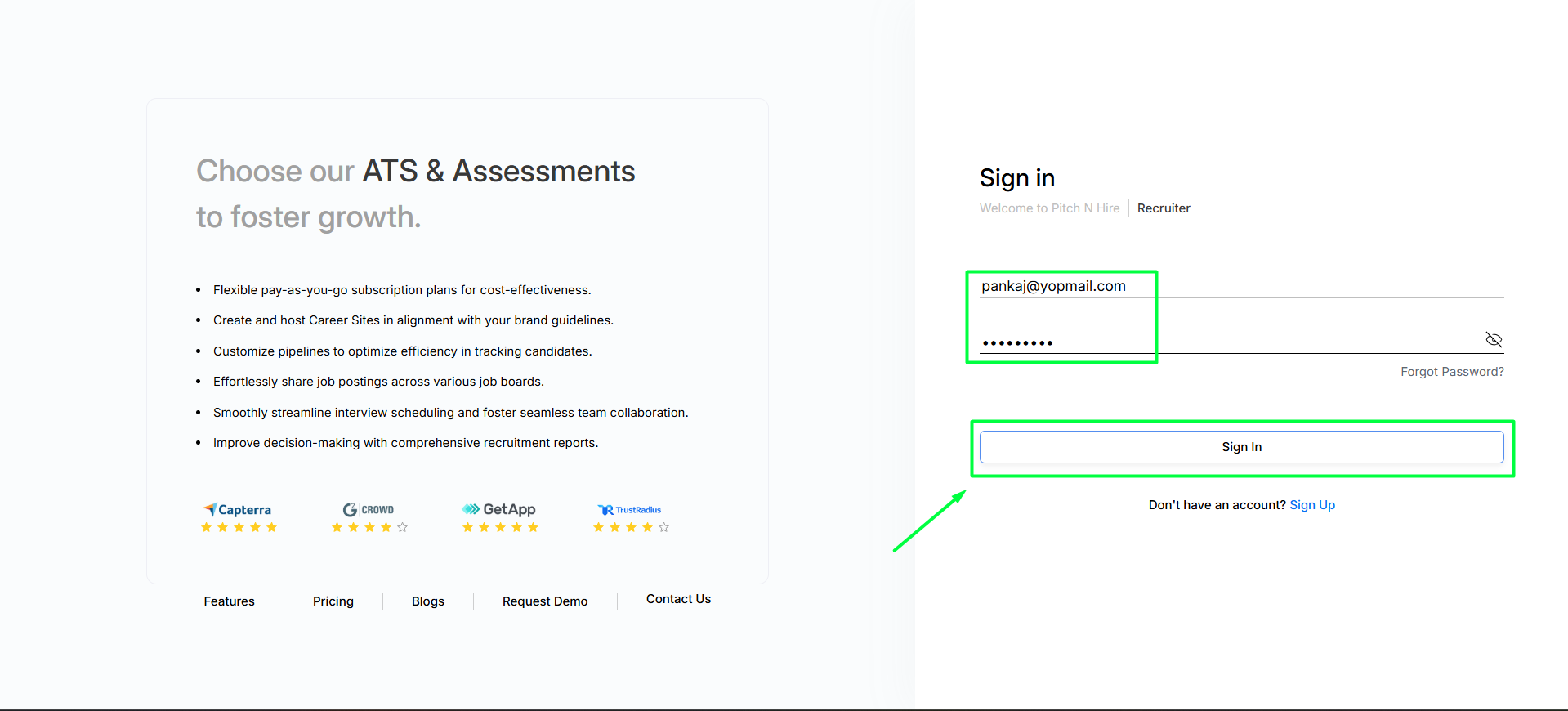
- Click on Login
- After login, actions are limited to the role’s permissions.
- Invitations: View all invited users with their assigned role.
- Resend Invite in case the user has not received the invitation mail.
- Delete Invite
- User Management: Edit or remove entered users using Edit and Delete options.
- Edit The User
- Delete The User
Permissions Matrix
Use the matrix below to configure permissions per role. The clusters group related entities.
Mark allowed actions when creating or editing a role.
| Cluster | Entity | create | read | update | delete | publish | invite | request data | stage change | show all | leave | remove user |
|---|---|---|---|---|---|---|---|---|---|---|---|---|
| Cluster Permission | application | read | update | delete | request data | stage change | show all | |||||
| assessment | candidate | create | read | update | delete | invite | ||||||
| job | job | create | read | update | delete | publish | ||||||
| client | client | create | read | update | delete | |||||||
| company | company | read | update | leave | remove user | |||||||
| user | user | create | read | update | delete | invite |
Notes:
- Cells shown with action names (e.g., read, update) indicate available permission toggles in the role editor. Empty cells are typically not applicable for that entity.
- Admin (Starter plan) typically has all permissions; Operator has a limited subset. In the Business plan, customize each permission for new roles.
Runtime Enforcement
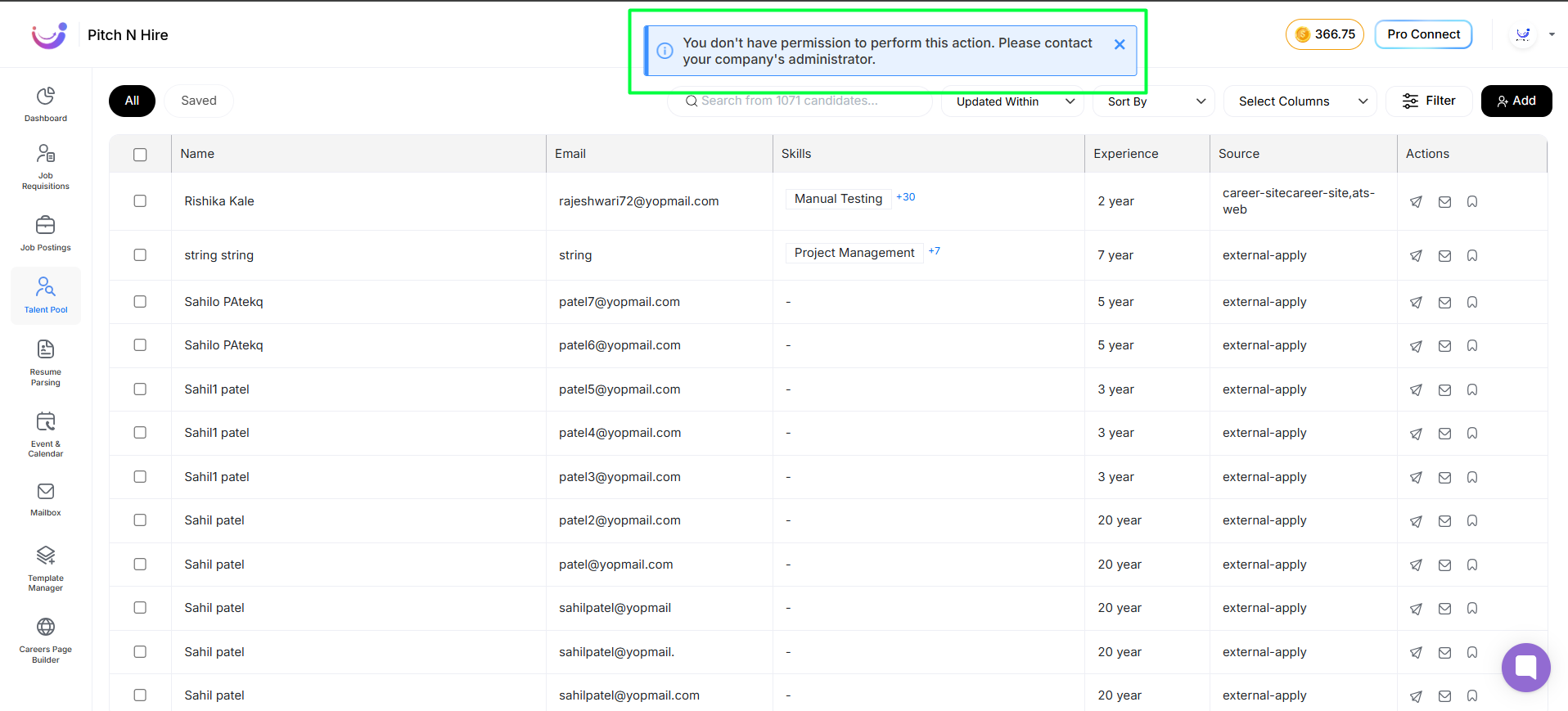
- After login, users can perform actions as per assigned role permissions.
- If a user attempts an action outside permissions, a warning is triggered and the action is blocked.
Example Setup (Business Plan)
- Create a role “Hiring Manager” with:
- job: create, read, update, publish
- application: read, stage change, request data
- Invite user and assign Hiring Manager role.
- User signs up/signs in and has access aligned with the defined permissions.